Living Security
Unify
Transform Human Risk into a Strong Security Culture and Proactive Defense with Unify Human Risk Management Platform
Top Challenges CISO’s and Security Leaders Face

How do we measure and quantify the human factor of cybersecurity risk?

What human behaviors are our biggest cybersecurity risks and how are we addressing them?
How do we show ROI and evolve our program to quickly address emerging human risks?
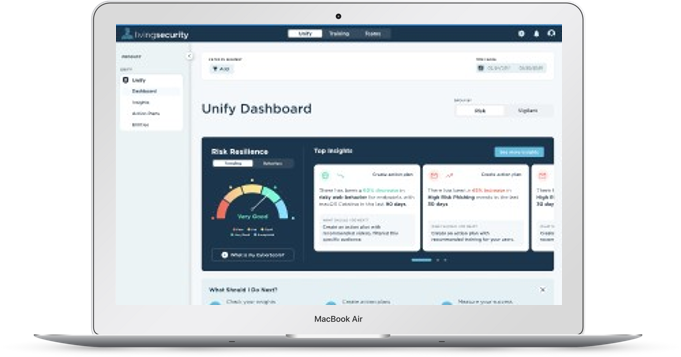
Introducing Unify Insights
Unify Insights, combined with Living Security’s industry leading Training, Teams, and Phishing provides all of the capabilities needed to fully implement Human Risk Management within your organization. These components allow the enterprise to manage the human risk and provide the content and engagement activities to provide focused and relevant training to specific groups of employees.
QUANTIFY RISK WITH ACTIONABLE INSIGHTS:
Aggregate the data from your various siloed security systems and actual human events to get clear and comprehensive insights to quantify your cybersecurity human risks including who, what, and where at any given moment.
Get answers:
What does our cybersecurity human risk picture look like?
How does our current risk align with our tolerance level?
Where is our risk high that we need to prioritize actions?
USE CASE
Unify in Action: Routinely Test Users Most Likely to be Successfully Phished
Overview: Ensure you are actively tracking your risk for employees who based on their role, tenure at the organization, and other factors are at a higher risk for phishing attempts. With Unify, you can recognize this group, track their behaviors and send them tailored training that is automatically adjusted as their behaviors and skills become more mature.
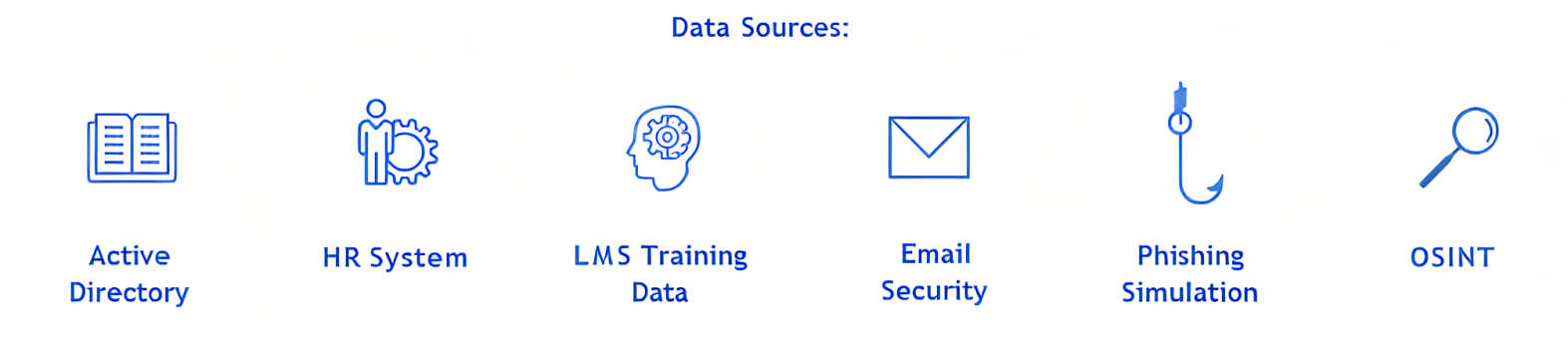
- Use characteristics about the user to identify which users are appealing to attackers (Active Directory & HR System)
- Identify the user’s current proficiency in phishing (LMS Training Data & Phishing Simulation) Understand what phishing types and tactics users struggle with
- Understand which users can be identified by an attacker or have information that is exposed externally (OSINT) Analyze the volume of spam and phishing attacks received by the user
- Correlate spam/phishing volume received to user’s overall URL and attachment click rates
- Automate Phishing simulation frequency for the
FOR MORE USE CASES, DOWNLOAD THE UNIFY ONE-PAGER NOW!

